SELF Chain Architecture
About SELF Chain & Entirety Chain
SELF Chain is the first blockchain in the Entirety Chain constellation. Entirety Chain is the broader infrastructure project encompassing enterprise blockchain solutions, AI consensus mechanisms (Proof-of-AI), constellation architecture, grid compute, and developer tooling.
For detailed technical documentation about Entirety Chain's full capabilities including Proof-of-AI consensus, Constellation architecture for enterprise chains, Grid Compute, and Security features, visit https://entiretychain.com.
Architecture Components
SELF Chain implements a revolutionary architecture combining AI and blockchain:
Blockchain Core - Advanced blockchain implementation
- Block structure with AI-enhanced validation
- Chain management with Proof of AI consensus
- High-performance transaction processing
Consensus (PoAI) - World's first Proof of AI mechanism
- AI-powered validator selection
- Reputation-based voting system
- Energy-efficient consensus
Networking - Enterprise-grade communication layer
- Secure P2P protocols
- TLS encryption throughout
- Cloud-optimized architecture
Storage - Local-first storage architecture
- User-controlled local databases
- SELF Chain for metadata and node discovery
- Optional user-controlled backup systems
- True data sovereignty without external dependencies
Cryptography - Post-quantum security
- Kyber key encapsulation
- SPHINCS+ signatures
- Hybrid cryptographic approach
AI Integration - Native AI validation system
- Pattern analysis for security
- Context management for transactions
- Intelligent validation services
Developer Resources
:::note For comprehensive developer documentation including SELF Studio, AI-native development, and detailed technical guides, visit https://entiretychain.com. :::
SELF Ecosystem Overview
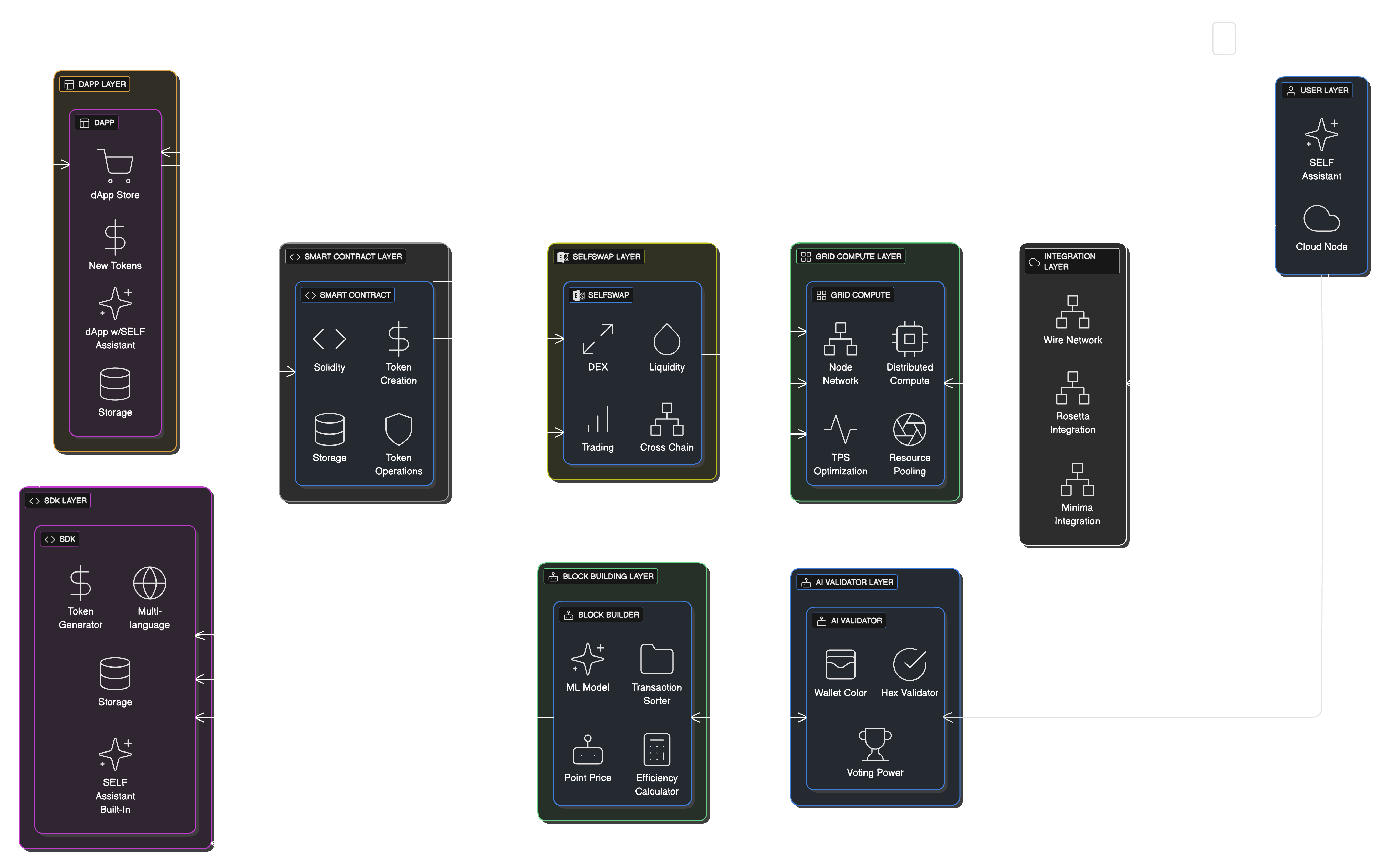
SaaS Platform Model
SELF Chain operates as a managed service platform:
User Node Provisioning
- Automatic node deployment when users create a SELF account
- Managed infrastructure with flexible access options
- Seamless user experience across different access levels
AI Model Integration
- Default AI model provided with each user account
- User-configurable AI preferences stored persistently
- Custom AI training with user preferences
App Integration
- Blockchain nodes integrated with SELF app
- Cross-app communication protocols
- Persistent user data synchronization
- Unified authentication and authorization
B2B Constellation Architecture
Entirety Chain Constellation
For detailed information about Constellation architecture, enterprise Layer-1 chains, and enterprise blockchain solutions, visit https://entiretychain.com.
SELF provides enterprise-grade blockchain solutions through the Entirety Chain constellation:
Corporate Layer-1 Chains
- Managed provisioning of parallel Layer-1 blockchains
- Similar to Polkadot parachains but for full Layer-1 chains
- Configurable AI model deployment for enterprise nodes
- Custom token generation capabilities
Enterprise Management
- SaaS management of corporate blockchain infrastructure
- Monitoring and health dashboards for enterprise clients
- Resource allocation and scaling for business needs
- Enterprise billing and subscription management
Ecosystem Interoperability
- Inter-chain communication between SELF and corporate chains
- Shared security and validation model
- Cross-chain transactions and data sharing
- Unified analytics and monitoring
Storage Architecture Revolution
Local-First Storage (Updated 2025-08-04)
SELF has adopted a Local-First Storage Architecture that prioritizes true data sovereignty and performance:
Core Principles
- Your Data, Your Server: All user data stays on the user's personal private cloud instance
- No External Dependencies: No reliance on IPFS, OrbitDB, or token-based storage
- Performance First: Local database queries in milliseconds, not seconds
- Optional Backups: Users choose who to trust with encrypted backups
Architecture Components
User's Personal Node (Private Cloud Instance):
├── Local Database (SQLite/RocksDB) ← Primary data storage
├── SELF Chain Connection ← Node discovery & metadata
├── AI Processing (OpenLLM) ← Local or cloud AI
└── Backup System (Optional) ← User-controlled replicationBenefits Over Distributed Storage
- Performance: 100x faster queries (local vs. distributed)
- True Privacy: Data never leaves your control
- No Fees: No token economics or storage provider costs
- Security: No central coordination servers to attack
- Simplicity: Standard database operations, no complex protocols
How It Works
- Data Storage: Your conversations, settings, and files live in your local database
- Node Discovery: SELF Chain blockchain stores only metadata (IP addresses, public keys)
- Communication: Direct encrypted connections between user nodes
- Backups: Optional encrypted replication to nodes you trust
This architecture delivers on SELF's core promise: true self-sovereignty with radical simplicity.
1. Core Architecture
1.1 Cloud-First Architecture
SELF Chain operates exclusively in a cloud-first environment:
Cloud Processing
- All operations occur in the cloud
- Distributed cloud nodes
- Secure cloud storage
- Cloud-optimized processing
Cloud Infrastructure
- Fully distributed cloud nodes
- Secure cloud storage
- Encrypted cloud communication
- Cloud-optimized infrastructure
Remote Access
- Cloud-only interaction model
- Secure cloud APIs
- Remote-first user experience
1.2 Network Architecture
1.2.1 Peer Discovery
- Periodic peer discovery from bootstrap nodes
- Peer-to-peer discovery through known peers
- Peer stats tracking and reliability scoring
- Network topology metrics
1.2.2 Message Routing
- Gossipsub for message propagation
- Kademlia for peer discovery
- Routing table with peer statistics
- Message forwarding with TTL
- Flood threshold protection
1.2.3 Connection Management
- Connection pooling per peer
- Connection timeout handling
- Active connection tracking
- Error handling and recovery
1.3 Storage Architecture
1.3.1 Local-First Storage
- User-controlled local databases
- SELF Chain for metadata and node discovery only
- Optional encrypted backups to user-chosen nodes
- True data sovereignty and integrity
1.3.2 Storage Features
- Distributed data storage
- Data versioning
- Data integrity verification
- Secure access control
2. Security Architecture
2.1 Network Security
Connection Security
- TLS encryption for all peer connections
- Message signing and verification
- Peer authentication
- Network message validation
Data Security
- End-to-end encryption
- Message integrity verification
- Secure data storage
- Access control
2.2 AI Security
AI Validation
- OpenLLM integration
- Context-aware validation
- Validator reputation system
- Secure AI processing
Security Features
- Secure cloud APIs
- Encrypted cloud channels
- Cloud node authentication
- Distributed cloud security
3. Performance Optimization
3.1 Network Optimization
3.1.1 Connection Pooling
- Limits concurrent connections per peer
- Prevents resource exhaustion
- Optimizes network bandwidth usage
- Reduces connection overhead
3.1.2 Routing Optimization
- Intelligent peer selection
- Path optimization
- Load balancing
- Error recovery
3.2 Storage Optimization
- Optimized data synchronization
- Efficient data retrieval
- Resource utilization
- Performance monitoring
4. Monitoring and Metrics
4.1 Network Metrics
- Peer connection statistics
- Message latency
- Network throughput
- Error rates
- Peer reliability scores
4.2 Performance Metrics
- Connection pool utilization
- Message delivery success rates
- Network congestion levels
- Resource usage
- Storage performance
5. Future Enhancements
5.1 Network Improvements
- Advanced peer selection algorithms
- Dynamic routing optimization
- Enhanced security features
- Improved error recovery
- Advanced monitoring capabilities
5.2 Storage Improvements
- Enhanced data synchronization
- Improved data integrity
- Optimized storage performance
- Advanced access control
5.3 Security Enhancements
- Enhanced cloud security
- Improved encryption
- Better access controls
- Advanced monitoring

